How to Analyze a Phishing Mail Part 2 - Email Header Analysis
- Anand R Menon
- Dec 7, 2023
- 5 min read

In Part 1, we explored ways to analyze the email body of a phishing mail. While the email body is the core content of the email which is easily visible to an end user, email headers form the metadata of the email which sheds more light into the origin, route and legitimacy of the email. In Part 2 of this 3-part series, we're focusing on the email headers and ways to decipher and analyze them.
What is an Email Header?
An email header is a set of metadata that accompanies an email message, typically hidden from the recipient's view. It contains information about the message's transmission, routing, and the sender and recipient's email addresses. Email header analysis is a crucial technique in the field of phishing analysis and email security which involves dissecting the information contained within the email header to uncover valuable insights about the message's origin, path, and authenticity. Understanding email headers is essential in identifying and mitigating phishing attacks, as attackers often manipulate or forge these headers to deceive recipients.
Key fields in an Email Header
Return Path: The email address where non-delivery notifications are sent.
Received: A series of headers detailing the email's route through various email servers. The bottom "received" entry will show the initial server which handled the message.
Authentication Results: Shows the status of email authentication protocols - SPF, DKIM, and DMARC. They help ensure that the email came from a legitimate source and hasn't been tampered with along the way.
SPF (Sender Policy Framework): SPF is like a bouncer for your email. It specifies which mail servers are authorized to send emails on behalf of your domain. When an email claiming to be from your domain arrives, the receiving server checks with SPF to see if it's on the VIP list. If not, it might get bounced like an uninvited guest at a fancy party.
DKIM (DomainKeys Identified Mail): DKIM signs your emails with a digital signature. It's like sealing an envelope with a wax stamp; when the recipient gets the email, they can verify the stamp to make sure it hasn't been tampered with. This ensures that the email came from the claimed sender and hasn't been messed with during transit.
DMARC (Domain-based Message Authentication, Reporting, and Conformance): DMARC is like the supervisor of SPF and DKIM. It tells the email receiver what to do if SPF or DKIM checks fail. It adds an extra layer of control and helps prevent phishing and spoofing. DMARC also provides a way for the email sender to get reports about email authentication failures, allowing them to fine-tune their setup.
Subject: Subject of the email
From: Sender of the email
To: Receiver of the email
Date: Date and Time of mail delivery to recipient
Reply-To: Specifies the email address to which replies should be sent. In many cases, "From" and "Reply-To" addresses are the same. If these addresses are different, there can be both legitimate and malicious scenarios for the same.
Legitimate scenario:
Automated Notifications: Automated systems or services might send emails on behalf of a user (From), but replies may be directed to a support team or specific contact (Reply-To).
Marketing and Communication Campaigns: Marketing emails may come from a general marketing address (From), but replies may be directed to a customer support or sales team (Reply-To).
Malicious scenario:
Spoofing and Impersonation: An email might appear to be from a known entity (From), but replies to the email may be directed to the attacker's address (Reply-To). This is a technique used in business email compromise (BEC) attacks.
X-headers: The "X-" prefix in email header fields typically denotes custom or non-standard headers that were added by specific email systems, applications, or servers for various purposes. These headers are not standardized by the Internet Engineering Task Force (IETF) and may vary between different email services or software. Some of the commonly seen X-headers are mentioned below.
X-Mailer: Indicates the email client or mail transfer agent (MTA) used by the sender to compose the email.
X-Priority: Specifies the priority of the email (e.g., High, Normal, Low).
X-Originating-IP: Displays the IP address of the sender.
Email Header Analysis Tools
Now, let's explore some tools which can be leveraged to effectively analyze email headers.
MX-Toolbox
Mx-Toolbox is a great suite of various email security products, "Email header analyzer" being one of them. Just copy-paste the email header to the Email Header Analyzer textbox and click on "Analyze Header".
Email Header Analyzer provides detailed view of the following:
-Email authentication(SPF/DKIM/DMARC Compliance)
-Email relay information(extracted from "Received" headers which lists down the various SMTP mail servers through which the email was relayed, related IPs and received time)
-Different email headers and their values in a tabular format
Also, note that there's an option at the bottom of the page to "Permanently forget this email header". In case of privacy and confidentiality concerns, use this option to remove any traces of the email header from MX Toolbox servers.
PhishTool
PhishTool is a powerful phishing email analysis tool. It helps organize the vast information contained in an email file into different logical sections and enables in-depth analysis of different aspects of a suspicious mail.
PhishTool divides email header information neatly into different sections such as Headers, Received Lines, X-headers, Security, Attachments and Message URLs. There is direct integration to VirusTotal, WhoIs services.
“Headers” section shows the basic header information such as “From”, “Display Name”, “To”, “Reply-To”, “Return-Path” etc.
“Received lines” section shows the sequence of hops between different SMTP servers till the email reaches its final destination.
“X-headers" section details the non-standard headers in the mail which was previously discussed.
“Security” section includes SPF, DKIM and DMARC authentication results of the email.
“Attachments” and “Message URLs” sections contain details regarding the email attachments and included URLs.
Sample Analysis
Now, as we're aware of the various email headers and ways to analyze them, let's do a sample analysis on the email headers of a suspicious mail.
To view the headers for the above mail, see the email raw file available at:
The email seems to come from Microsoft and mentions that an unusual sign-in activity was observed on the email recipient's account from Moscow, Russia. The email further suggests to report the user if this wasn't done by the email recipient themselves.
First, let's have a check on the "Display name", "From", "Reply-To" and "Return Path" addresses.
Here, the "Display Name" is "Microsoft account team". But, from the very first look on the "From" and "Reply-To" addresses, its clear that the mail isn't from Microsoft. Still, we can have an additional check on the domain mentioned in From address, "access-accsecurity[.]com". WhoIs details show that it belongs to "Name Strategies LLC" which is a telecommunications company based in Colorado, United States. Reply-To address is a personal mail account belonging to "gmail.com" domain which is a big red flag. "Return Path" is the mail to which non-delivery notifications are sent. The WhoIs search for the "Return Path"(thcultarfdes[.]co[.]uk) shows that this site is not even registered. This indicates that this is a forged email header. Attackers use a variety of tools and custom scripts to forge email headers. Another method seen is, using compromised SMTP servers or exploiting specific vulnerabilities present in those servers to forge email headers.
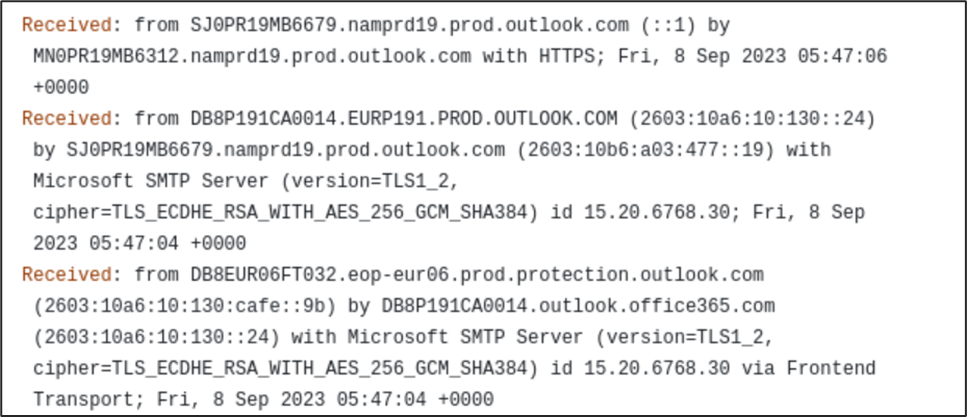
Now, lets have a check on the "Received" headers.
As discussed earlier, the order for Received headers is from bottom to top. Here, we can see the email passed between 4 different email servers. We don't have much details(eg. location) related to these servers apart from the fact that these are Microsoft SMTP servers. The first "Received" header mentions the IP "89[.]144[.]44[.]2"(This is the originating IP of the email) which belongs to GHOSTnet GmbH, Germany and has been reported multiple times for Phishing/Email Spam/Spoofing according to AbuseIPDB.
Now, let's have a look on the authentication section of the header.
SPF, DKIM and DMARC haven't been set which is highly suspicious. This means that there is no protection against spoofing for the sender's domain.
So, in this case, there are multiple red flags which lead us to the conclusion that the email is not from Microsoft and is indeed a phishing mail.
As part 2 of this phishing analysis series completes, we're done with the email header analysis. Let's go to Part 3 - Dynamic Analysis!!!























Comments